
 Image: Thinkstock
Image: Thinkstock
Batten down the hatches
It’s a tough, insecure world out there, fellow PC faithful. Times have never been scarier, with website data breaches turning into regular affairs, programming flaws like Heartbleed popping up left and right, and botnets like Gameover Zeus infecting a legion of PCs, only to gobble the up personal information and financial data stored within.
Good news: There’s a lot that regular PC users can do to protect themselves against the worst of the worst. But bad news: Most of us don’t bother.
Giving your digital life a thorough security overhaul is easier than you’d think. Here are 10 critical security measures you should be doing right now—go ahead, do it!
Use a password manager
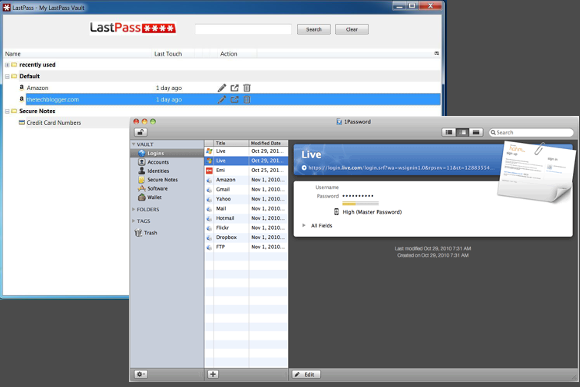
Saying that passwords are dead is a popular meme. Until someone figures out a viable and universal replacement, however, we’re stuck with them.
Alas, passwords are a pain, since you should be using a long string of random letters, numbers, and special characters for all your critical accounts. Passwords that complex are as difficult to remember as they are to crack—which is why using a password manager that can generate and save those passwords for you is so crucial.
Password Mangers are easy to use, and most are cross-platform, giving you access to the data on PCs and mobile devices alike. Our favorites include LastPass, Dashlane, 1Password, and KeePass.
Two-factor authentication

Two-factor authentication is a second step that bolsters the strength of all those long, random passwords you’re now using. This security measure is based on the notion that you need two items to prove your identity: Something you know and something you have. The “something you know” is your regular password, and the “something you have” is usually a short, one-time code generated via text massage or smartphone app that you need to enter before logging in.
Two-factor authentication is not foolproof, but it’s far stronger than using passwords alone. Google’s Authenticator app for Android, iOS, and Blackberry 4.5-7.0 is a popular choice for generating one-time codes, but there’s also the cloud-sync service Authy for Android, iOS, Linux, Mac, and Windows.
Back up your data… twice

Backing up your data may not seem like a security matter, but guarding your data against faulty hardware or a devastating virus that wipes out your hard drive is extremely important. For best results, don’t just back up to an external hard drive at home. You should also back up to an offsite location to protect against fire, burglary, or children carrying water.
Online backup is the easiest way to get offsite protection. The numerous services available include Backblaze, Carbonite, CrashPlan, iDrive, and Mozy. A disaster-proof backup scheme doesn’t have to cost you a dime, though, if you’re willing to do a wee bit more legwork.
Create your own private Internet tunnel

Most public, shared Wi-Fi networks are wide-open. A hacker equipped with a few trivial programs can snag your online traffic as it flies by.
This is mitigated somewhat by logging into websites using HTTPS, but it’s not a perfect solution. Ideally, you should be using a virtual private network to create an encrypted tunnel between your device and the Internet. There are free options from companies such as Hide My Ass, Hotspot Shield, and Tunnel Bear, but a paid VPN is the better option if at all possible. A year of Hide My Ass is just $60 and covers you across PCs and mobile devices.
Lock down your router

Your home Wi-Fi router is probably the most sensitive Internet connection in your life, since home is where you’re most likely to view your bank accounts and other sensitive information online. But alas, most people stick to basic or—shudder—default passwords for their home network.
For the best home Wi-Fi security, use WPA2 encryption and a randomly generated login password that is at least 30 characters long. The longer and more random it is, the harder it is to crack (the occasional flaw in router firmware aside). Can’t remember a 30-character password? Save it in your password manager. Finally, don’t forget to change the user name and password for your router’s admin panel.
Cut the daisy chain

Another weak spot in online security: Email accounts that receive password-recovery messages, in the event you get locked out of your account. Recovery accounts are also prime targets for hackers looking to penetrate your online life.
The best defense is to use a single, hard-to-guess recovery address—something like “[email protected]”—and use it only for emergency recovery.
The worst solution is to daisy-chain all your critical accounts—your Outlook.com address is the recovery address for your Gmail address, and Gmail is the recovery address for Amazon. All it takes is one break in the daisy chain to ruin your entire online life.
Ditch Java (if you can)

Oracle’s Java is no longer critical software for many PC users. That’s a good thing, because it’s been the source of a veritable flood of security vulnerabilities. Some security experts are calling for Oracle to rewrite Java. In January, 2013, the Department of Homeland Security’s US-CERT (Computer Emergency Response Team) recommended that all PC users disable Java unless they absolutely need it.
The best way to find out if you can live without Java is to delete it completely. Seriously! Go do it right now. If a website or software prompt demands Java in the future, simply reinstall it—but you probably won’t have to.
Encrypt everything

When Google learned the NSA was intercepting traffic from its internal networks, the company’s answer was simple: encrypt everything. And you should, too. Forcing websites to use encryption whenever possible—with browser plug-ins such as the Electronic Frontier Foundation’s HTTPS Everywhere, if need be—keeps no-goodniks from swiping your logins and personal information.
Don’t stop at websites, though. If you carry personal data on a USB stick, encrypt it with Microsoft’s BitLocker to Go, or create encrypted file containers via the Disk Utility in Mac OS X. Open-source encryption options for Windows include FreeOTFE or DiskCryptor. Encrypt your external hard drives, too—especially your backups.
Supplement your antivirus with an on-demand anti-malware scanner

To stay as safe as possible on Windows, it’s best to equip your PC with two security programs: one antivirus and one anti-malware. The antivirus programs, such as AVG Free or Avast, are always-on solutions that scan incoming files and websites for malicious intent.
These programs won’t necessarily catch or remove everything. That’s why it’s a good idea to periodically run an anti-malware program, which stands a better chance of catching active and cutting-edge problems. Snag MalwareBytes Anti-Malware Free (or an alternative) and run it weekly.
Tape that webcam

Malware was bad enough when it randomly distributed your Word documents to all your email contacts. It can get much worse, now that computers have the capability to see and hear us via webcams and microphones.
Luckily, there’s an easy defense against peeping webcams: plain, old adhesive tape. Just take a small piece of that and cover the lens. When you need to use your webcam, just peel it off and replace it later. If you’re worried about putting tape on the lens, use paper and tape instead.
It’s a bit of a kludge, but hey: Tape has the added benefit of being impenetrable to software attacks.


