
 Image: Project Zero
Image: Project Zero
Intel chief executive Brian Krzanich told investors Thursday afternoon that the company plans to release silicon with built-in mitigations to the Spectre and Meltdown vulnerabiities later this year, a statement that raises more questions than it answers.
For Intel, it really has been a Tale of Two Cities scenario: Intel reported the best quarter in its history, as fourth-quarter 2017 revenue grew 4 percent year-over-year to $17.1 billion. But Intel has also been the face of Spectre and Meltdown, two critical vulnerabilities built into basically every processor it ships into the PC and server markets.
Why this matters: Intel has been busy working with PC makers and OS vendors like Microsoft to release microcode that includes so-called mitigations, microcode updates that patch the vulnerabilities. But even that hasn’t gone so well: Intel advised end users to stop applying patches after systems unexpectedly rebooted. Now, Intel has revealed it’s working on a more permanent fix, but the impact on users remains unknown.
‘Security is a top priority’
“Security is a top priority for Intel, foundational to our products, and it’s critical to the expanse of our data-centric strategy” Krzanich told investors in a conference call. “Our near-term focus is on delivering high-quality mitigations to protect our customers’ infrastructure from these exploits. We’re working to create silicon-based changes to future products, that will directly address the Spectre and Meltdown threats in hardware. And those products will begin appearing later this year.”
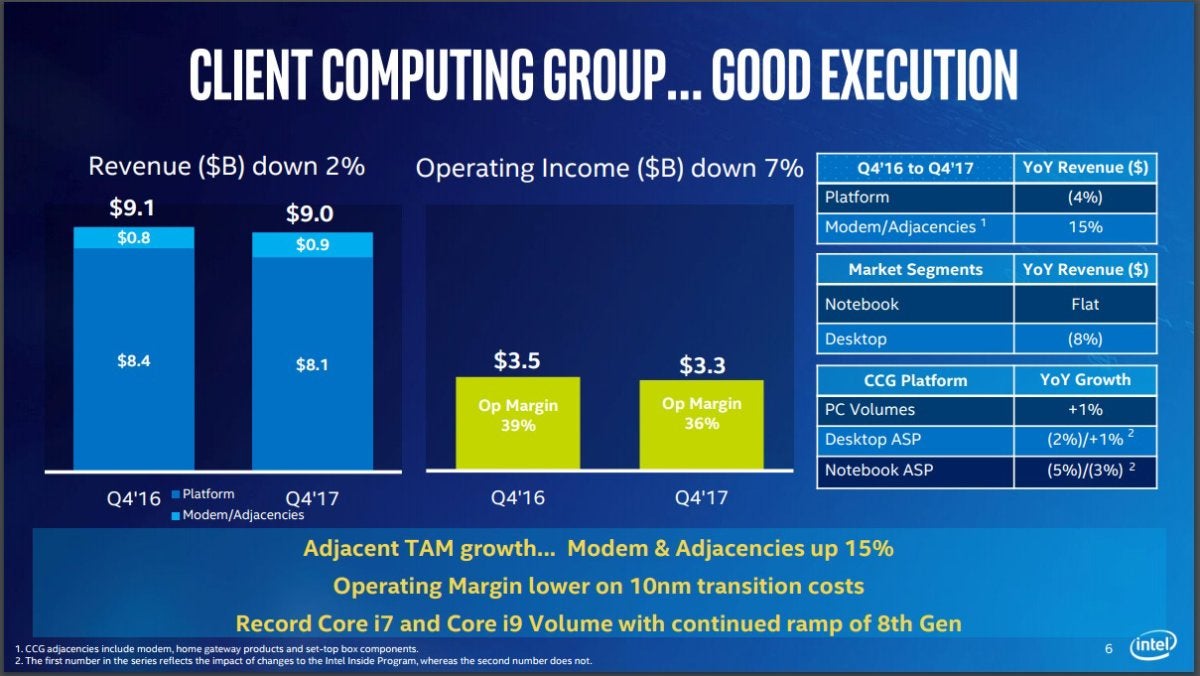
Intel’s Client Computing Group reported a sales decline of 2 percent to $9 billion. Notebook revenue was flat, while sales into desktop PCs declined by 8 percent.
 Intel
Intel Intel’s Client Computing Group did fairly well in a tough PC market.
Krzanich reiterated that the vulnerabilities won’t have an effect on future sales. “I can tell you, at the highest level, that we’re not seeing much of a change in those forecasts as a result of this,” he said of the discovery of the vulnerabilities and their mitigations.
“I’ve assigned some of the very best minds at Intel to work through this,” Krzanich added.
6 questions Intel needs to answer
The Wall Street analyst community had several chances to pin down Krzanich on Intel’s silicon security strategy. Instead, they peppered Krzanich with questions about the company’s proposed capital expenditures and memory plans.
Important questions about the silicon fix remain hanging for end users and corporate customers. Here’s what we wished the analysts had asked, and our best guesses as to the answers.
1. When exactly will the silicon fixes take place?
Our guess: the end of 2018. Based upon leaked product roadmaps, that would probably mean the reported “Cascade Lake-X” 14-nm parts, as well as possibly the 10-nm “Cannon Lake” parts due sometime thereafter.
Note that Pat Moorhead, a corporate fellow at AMD and now the principal analyst at Moor Insights, disagrees. “I believe these mitigations are already built in or we would see a year delay in new chips,” he said in a message. So it’s possible that chips releasing sooner, such as Coffee Lake-S, might include these fixes.
2. Will these fixes solve both Spectre and Meltdown vulnerabilities?
Our guess: Just Meltdown. As our Spectre and Meltdown FAQ explains, Meltdown most strongly affects Intel processors because of the aggressive way those chips handle speculative execution. Spectre appears to require a more fundamental redesign.
3. Will the mitigations apply only to new products, or older chips, too?
Our guess: only new PC microprocessors, though potentially Intel could re-spin existing processors, especially for cloud servers. Doing so, however, would open up the possibility of an actual recall, something that Intel doesn’t seem to be indicating as part of its “everything-is-fine” guidance. To reassure customers, some chips might carry a suffix to assure buyers that the mitigations are built in.
4. What effect will those mitigations have on the chip itself?
Our guess: Any time you add logic to a CPU, and physically increase its size, the cost is affected as well. But whether Intel would have to add dedicated logic blocks, or simply restructure the chip, isn’t known. If there were additional costs that raised prices, Intel would eat it.
5. How will performance be affected?
Our guess: The only guidance we have is what our tests have shown: little effect in CPU-dependent benchmarks, but more significant slowdowns in broader tests of system performance.
6. Will silicon with built-in mitigations boost PC sales?
Our guess: In consumer PCs, probably not. In enterprises, it’s more likely to be seen as a selling point. Businesses won’t want to risk exposing themselves to lawsuits, and any smart PC salesperson will remind them of this. Consumers will just grit their teeth and bear the slowdown and the lack of available GPUs.
“I think we could see some increased demand for servers, but not for PCs, as I do not think many will notice the performance degradation,” Moorhead said.
Again, our guesses are just that. Let’s hope that Intel starts laying out plans for solving Spectre and Meltdown in silicon, and does it soon.


