
 Image: Alaina Yee / Foundry
Image: Alaina Yee / Foundry
The more we live our lives digitally, the more important it is to keep our computers and other devices safe from data loss, fraud, and spying.
Although most people today use phones more than computers, it is computers that need the most attention. Both Windows and Mac OS are more capable operating systems than Android and iOS, but because more can be done on a computer, the potential for problems is also greater.
Computer security is about protecting a computer from unauthorized use, malware, and espionage. For most people data security is at least as important, i.e. not losing irreplaceable files such as private photos and videos. Data security depends on computer security, but not vice versa. Even if you don’t have a single irreplaceable file on your computer but use a web browser to check your emails or log in to your bank, for example, you still benefit from computer security.
No amount of antivirus software, encryption, and other computer protection can protect your priceless files from being lost in a fire or stolen, for example. It’s little comfort that a thief can’t look at your holiday photos when you can’t because you had no backup.
Antivirus – a piece of the puzzle
our favorite antivirus program for windows
Norton 360 Deluxe
 Read our reviewPrice When Reviewed:$49.99 for the first yearBest Prices Today:$19.99 at PCWorld Software Store | $49.99 at Norton
Read our reviewPrice When Reviewed:$49.99 for the first yearBest Prices Today:$19.99 at PCWorld Software Store | $49.99 at Norton
Viruses, Trojans, and other malware were more common 15 years ago, but cause more damage today. The most common category of malware to fall victim to today is ransomware, which encrypts all the contents of your computer and demands a ransom so you don’t throw away the key.
Ransomware costs society billions every year. For home users, the sums required are astronomical, and even those who pay risk being caught out as some extortion programs are simply deceptive and never save an encryption key.
If you run Windows, a good antivirus program is still recommended, although the built-in Windows Defender function is now really competent at stopping known malware.
As well as often being slightly better at detecting known malware, the best antivirus programs have features that can stop previously unknown malware from constantly monitoring what’s happening on your computer. For example, they can detect that files are being encrypted and quickly stop the program performing the encryption. If it’s ransomware, it may only have time to encrypt a few files, and if it’s something legitimate (you may have chosen to encrypt sensitive files), just unblock it.
To avoid being affected, however, it’s not enough to install an antivirus and pat yourself on the back. You can only be truly protected with a multi-pronged approach.
Further reading: Best antivirus for Windows PCs
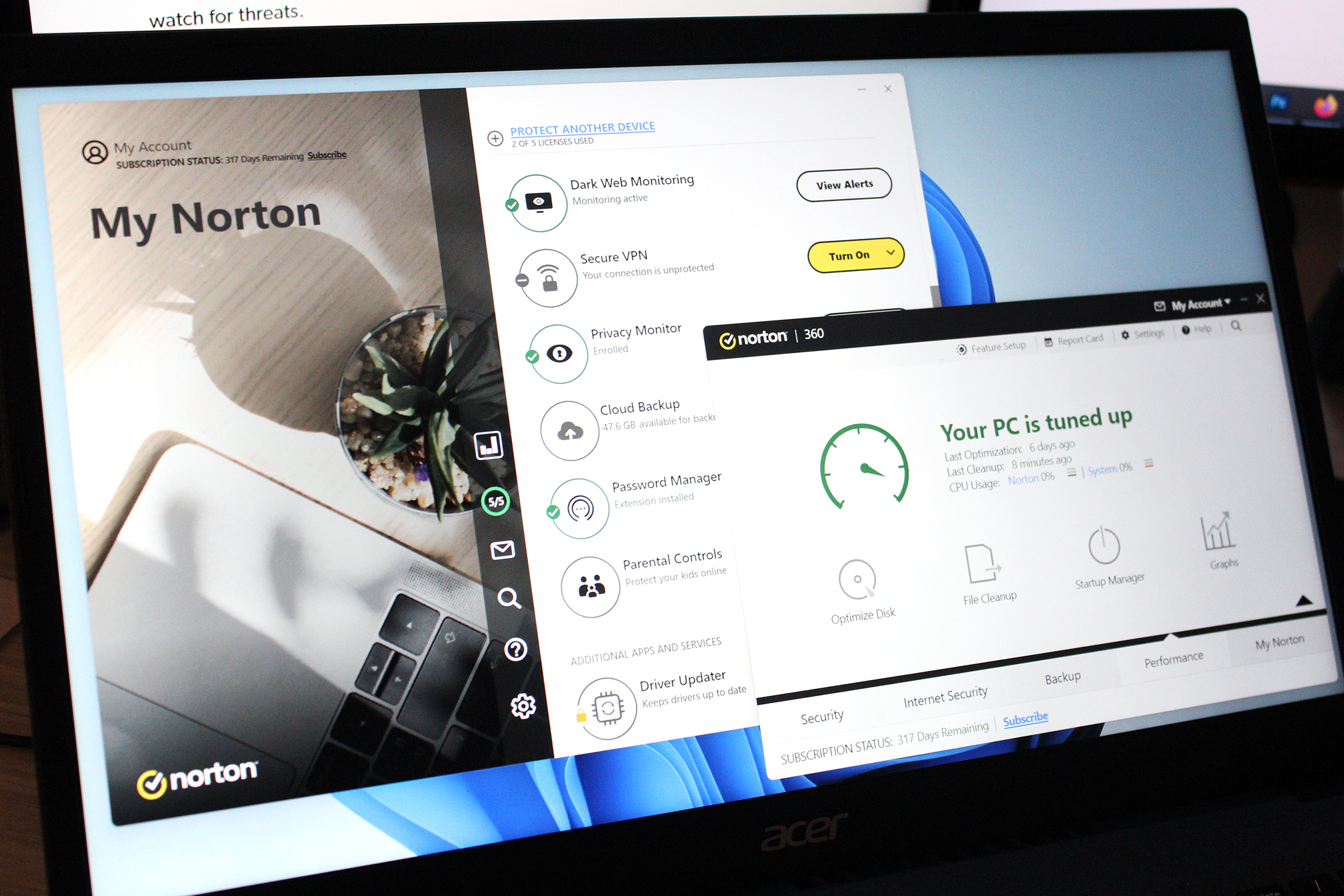
Keep Windows and programs up to date
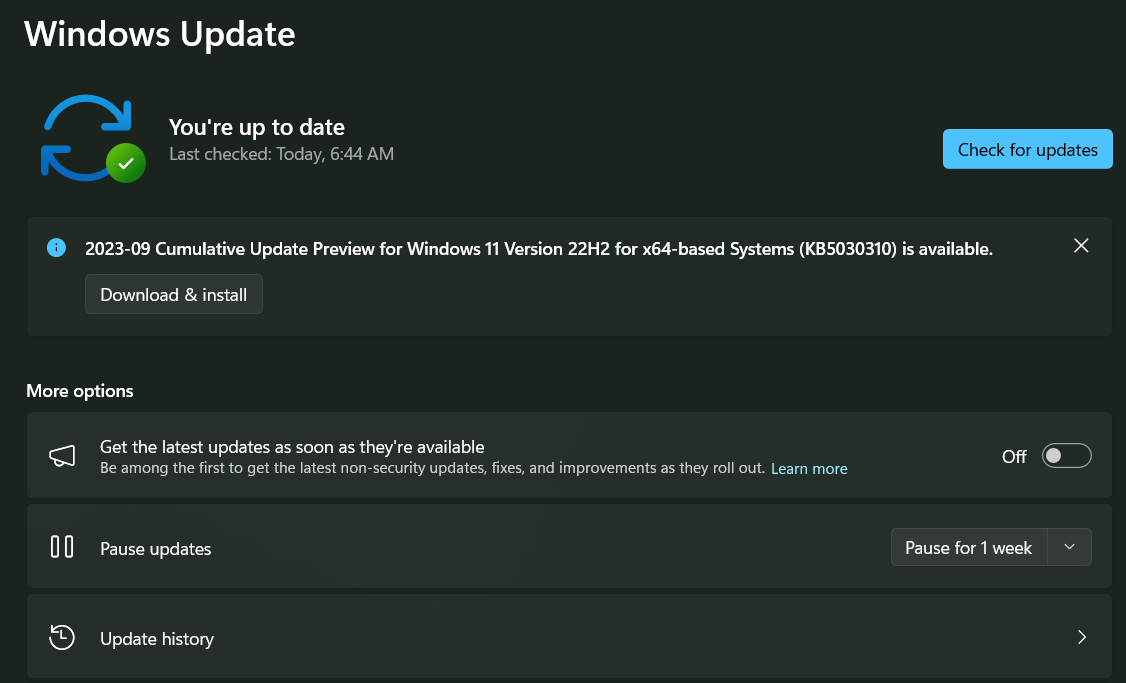
Make sure to keep Windows up to date.
Make sure to keep Windows up to date.
Brad Chacos/IDG
Make sure to keep Windows up to date.
Brad Chacos/IDG
Brad Chacos/IDG
Just as important as an antivirus program is updated software. New security flaws are constantly being discovered, and not updating Windows and installed programs puts you at an unnecessary risk of being hit by malware.
By far the most important thing to keep updated is Windows and all the browsers you use. Chrome, Firefox, Brave and most other browsers have automatic updates enabled by default and many can display a notification when an update has been downloaded and can be installed by restarting the browser. Windows also displays an icon in the notification bar to indicate that there are pending updates.
All applications used for communication are also particularly vulnerable and important to keep updated: email clients like Outlook and Thunderbird, chat applications like Slack and Discord. The same goes for programs that open files coming from others, such as Acrobat and Word.
A trick for programs you can’t update
In principle, it’s best to keep all programs updated to the latest version, but I know from experience that there may be programs you can’t or don’t want to update — for example, because newer versions don’t work as well or your license is only for a certain version. One way to increase the security of such programs is to install them in a virtual machine using, for example, VMware Workstation. This works well for applications you don’t use very often, and as long as the application doesn’t have high graphics performance requirements. This is how security researchers analyze detected malware without infecting the entire computer.

Ed Hardie
Ed Hardie
Ed Hardie
The most common ways to get hit by malware
Of course, even if your antivirus software is really good and you have all other protections enabled on your computer, the best thing to do is to stay away from potential malware as much as possible.
Malware usually arrives on your computer as email attachments (can come from spam or from contacts who have been affected themselves), via social media links, in files automatically downloaded from websites, embedded in pirated programs (Adobe Photoshop is a popular target), and via legitimate programs whose developers have been hacked.
A common ploy to trick you into downloading and running malware on the web is to display a fake alert claiming that you have been affected by viruses, for example, and urging you to run an “antivirus” program. More sophisticated variants have very well-crafted fake dialog boxes with the same design as genuine Windows alerts.
In recent years, it has also become more common for malware to be installed automatically as soon as you visit a website. This type of attack is behind many of the security updates that Microsoft, Google, and other companies release from time to time for their browsers — so users who don’t update are at risk of being caught by, for example, an extortion program without having done anything else risky like opening an unknown attachment or clicking on a dodgy link.
Pay attention to what you give admin permissions for
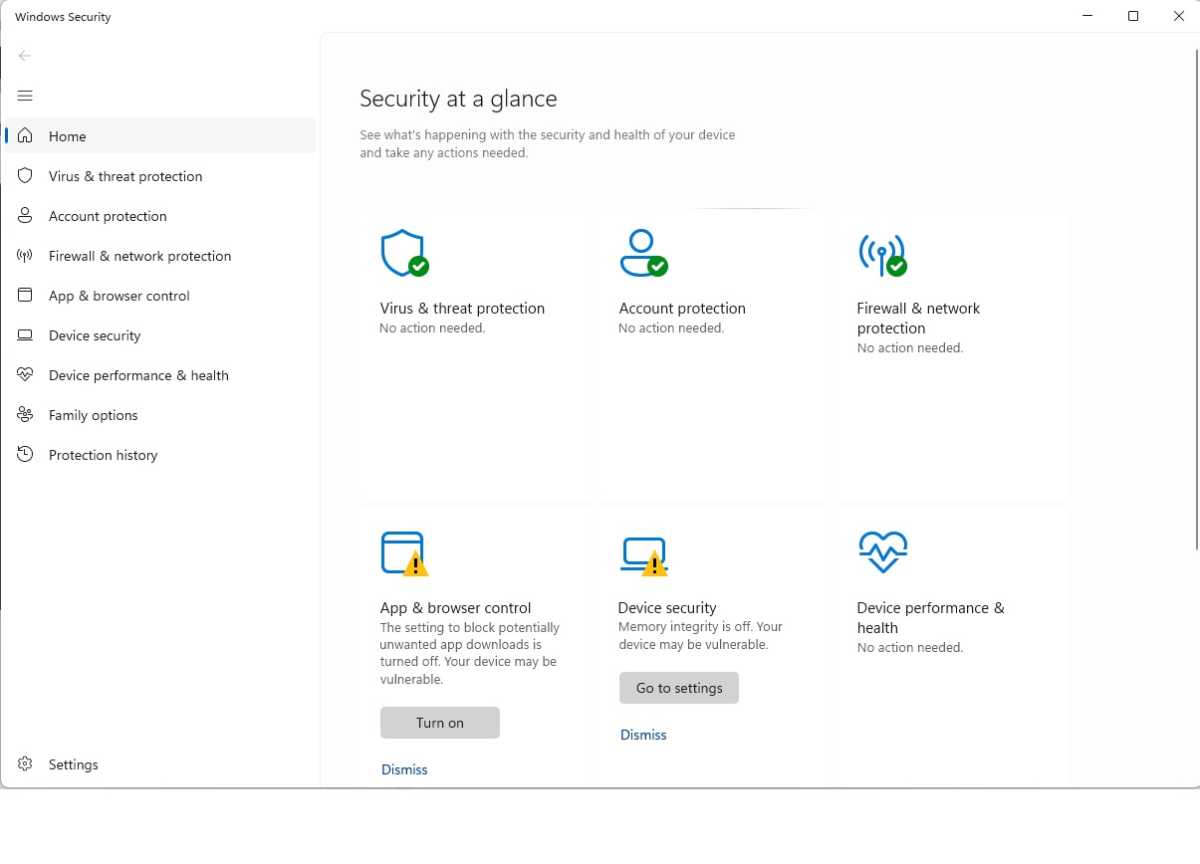
Follow the recommendations in Windows Security for optimum protection.
Follow the recommendations in Windows Security for optimum protection.
Foundry
Follow the recommendations in Windows Security for optimum protection.
Foundry
Foundry
Some malware needs the help of the user to infect the computer. This is mostly because it’s much easier than having to find and exploit some unknown security flaw to automatically bypass Windows’ various protections.
These so-called Trojans (named after the Trojan horse) infect your computer after you as a user do two things:
1. Open a downloaded file, and 2. give the program that launches it admin privileges via the standard Windows “Do you want this app to make changes to your device?” dialog.
Since most legitimate applications also need admin permission to install, it’s easy to click away all such dialogs without looking too closely. This is exactly what Trojan developers are counting on, so it’s a good habit to start checking these dialogs every time they appear.

Claudio Schwartz
Claudio Schwartz
Claudio Schwartz
Backing up
Backup is essential if you want to protect your priceless files from threats such as ransomware, fire, and theft. Having only one copy of a file is the same as having no copy at all. It is best to have at least three copies in at least two different places. For example, this could be an online backup such as iDrive and a backup to an external hard drive using a program such as R-Drive Image.
Better still, have at least one backup that you can’t delete directly from your computer but have to log in to an account secured with two-factor authentication to delete.
Further reading: Best Windows backup softwareFurther reading: Best cloud backup services
our favorite online backup service
iDrive Online Cloud Backup

 Read our reviewPrice When Reviewed:$79.50Best Prices Today:$79.50 at iDrive
Read our reviewPrice When Reviewed:$79.50Best Prices Today:$79.50 at iDrive
Encrypt sensitive files – or the entire disc
Where backup is about protecting files from being lost, encryption is about protecting files from being read by anyone but you. On mobile phones, encryption is automatic and comprehensive on both Android and iOS, as well as on modern Macs.
On Windows, it’s a little trickier, but it can be done. A Pro license on Windows includes the Bitlocker feature, which encrypts the entire disk. A free alternative is Veracrypt, which can both encrypt the entire disk and create encrypted disk images where you can hide the most sensitive files.
Further reading: How to encrypt files in Windows
This article was translated from Swedish to English and originally appeared on pcforalla.se.


