
 Image: Tor
Image: Tor
Recently, BoingBoing ran an article about how some librarians in Massachusetts were installing Tor software in all their public PCs to anonymize the browsing habits of their patrons. The librarians are doing this as a stand against passive government surveillance as well as companies that track users online and build dossiers to serve highly-targeted advertising.
It’s an interesting project and a bold stand for user privacy. But the good news is that if you want to browse anonymously, you don’t have to go to the library to use Tor. Connecting to the Tor network from your own PC is quick and painless thanks to the Tor project’s dead simple Tor Browser. (Want even more privacy? Check out the top picks from our VPN reviews.)
What is Tor?
Tor is a computer network run by volunteers worldwide. Each volunteer runs what is called a relay, which is just a computer that runs software allowing users to connect to the Internet via the Tor network.
Before hitting the open Internet, the Tor Browser will connect to several different relays, wiping its tracks each step of the way, making it difficult to figure out where, and who, you really are.
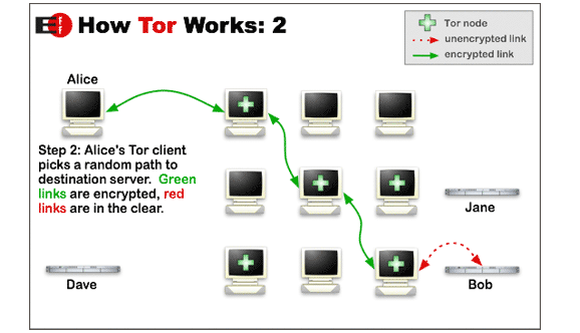
While Tor is gaining a reputation as a tool for buying illicit goods online, the software has numerous legitimate uses. Activists masking their location from oppressive regimes and journalists communicating with anonymous sources are two simple examples.
If, like the librarians in Massachusetts, you don’t have an exotic reason for using Tor, it’s still a good tool to keep your browsing private from your ISP, advertisers, or passive government data collection. But if the NSA or other three-letter agency decided to actively target your browsing habits that’s a whole different ballgame.
Getting started
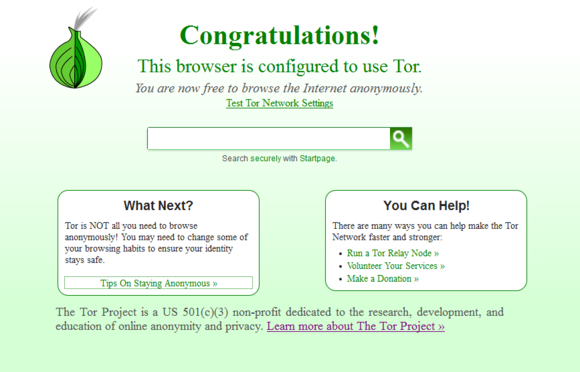
The easiest way to use Tor is to download the Tor Browser. This is a modified version of Firefox along with a bunch of other software that connects you to the Tor network.
Once you’ve downloaded the installer, you have two options: You can just install the software or you can check the installation file’s GPG signature first. Some people like to check the installation file to make sure they’ve downloaded the proper version of the browser and not something that’s been tampered with.
But checking the GPG signature is not a painless process and requires an additional software download. Nevertheless, if that’s something you’d like to do, the Tor Project has a how-to explaining what’s required.
Installing Tor
Whether or not you’ve checked the GPG signature, the next step is to install the Tor browser itself.
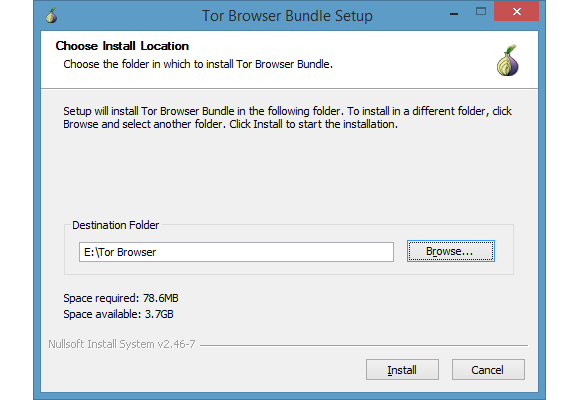
You can install the Tor browser on a USB stick.
For Windows, the Tor Browser comes as an EXE file, so it’s basically like installing any other program. The key difference is that the browser doesn’t have the same default location as most programs. Instead, it offers your desktop as the install location.
The Tor browser does this because it is portable software and doesn’t integrate into a Windows system the way typical programs do. This means you can run the Tor browser from almost anywhere—the Desktop, your documents folder, or even a USB drive.
When you arrive at the Choose install location window Click Browse… and then choose where you’d like to install the browser. As you can see in the image above, I installed it to a USB drive that I tote around on my key chain.
Once you’ve got your location selected, just press Install and Tor takes care of the rest.
Using the Tor Browser
Once the browser is installed, you’ll have a plain old folder called Tor Browser. Open that and inside you’ll see “Start Tor Browser.exe”. Click that file and a new window opens asking whether you’d like to connect directly to the Tor network or if you need to configure proxy settings first.
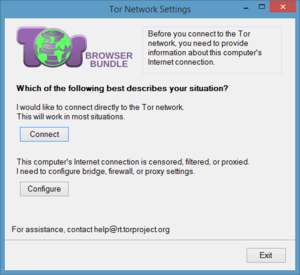
Most people can simply connect directly to the Tor network to get started. (Click to enlarge.)
For most people, choosing the direct option is best, so choose Connect. A few seconds later a version of Firefox will launch and you are now connected to the Tor network and able to browser in relative anonymity.
To make sure you’re connected to Tor go to whatismyip.com, which will automatically detect your location based on your Internet Protocol address. If your browser shows you coming from a location that is not your own, you are good to go. Just make sure you do all your anonymous browsing from the Tor Browser itself as other programs on your system are not connected to Tor.
But browsing anonymously on Tor isn’t quite as easy as booting up a program. There are also some rules of the road you should observe, such as connecting to every site possible via SSL/TSL encryption (HTTPS). If you don’t, then anything you do online can be observed by the person running your exit node. The browser has the Electronic Frontier Foundation’s HTTPS Everywhere add-on installed by default, which should cover your SSL/TSL needs most of the time.
The Tor Project has more tips on browsing anonymously.
Also, remember that browsing in anonymity does not make you immune to viruses and other malware. If you are going to the seedier parts of the Internet, Tor cannot protect you from malicious software that could be used to reveal your location.
For the average Internet user, however, the Tor Browser should be enough to stay private online.



