
 Image: Google/Natascha Eibl
Image: Google/Natascha Eibl
Massive security vulnerabilities in modern CPUs are forcing a redesign of the kernel software at the heart of all major operating systems. Since the issues—dubbed Meltdown and Spectre—exist in the CPU hardware itself, Windows, Linux, Android, macOS, iOS, Chromebooks, and other operating systems all need to protect against the first exploits that have begun circulating. And worse, plugging the hole can negatively affect your PC’s performance.
Everyday home users shouldn’t panic too much, though some proof-of-concept exploits are being circulated in the field. Just apply all—well, most—available updates and keep your antivirus software vigilant, as ever. If you want to dive right into the action without all the background information, we’ve also created a focused guide on how to protect your PC against Meltdown and Spectre.
Here’s a high-level look at what you need to know about Meltdown and Spectre, in plain language. Be sure to read Google’s post on the CPU vulnerabilities if you like diving deep into technical details.
#id664c736e55c41 .jw-wrapper::before { content: “” !important; }
Meltdown and Spectre CPU flaw FAQ
Editor’s note: This article was most recently updated to mention Intel releasing fixed Spectre patches for Kaby Lake and Coffee Lake CPUs, and link to PCWorld’s guide on checking Meltdown and Spectre’s performance impact on your computer.
Give it to me straight—what’s the issue here?
Again, the CPU exploits in play here are extremely technical, but in a nutshell, the exploit allows access to your operating system’s sacrosanct kernel memory because of how the processors handle “speculative execution,” which modern chips perform to increase performance. An attacker can exploit these CPU vulnerabilities to expose extremely sensitive data in the protected kernel memory, including passwords, cryptographic keys, personal photos, emails, or any other data on your PC.
Meltdown is the more serious exploit, and the one that operating systems are rushing to fix. It “breaks the most fundamental isolation between user applications and the operating system,” according to Google. This flaw most strongly affects Intel processors because of the aggressive way they handle speculative execution, though a few ARM cores are also susceptible.
 Gordon Mah Ung
Gordon Mah UngEven new Intel chips like the Core i7-8700K are affected by Meltdown and Spectre.
Spectre affects AMD and ARM processors as well as Intel CPUs, which means mobile devices are also at risk. (We have a separate FAQ on how Spectre affects phones and tablets.) There may be no permanent hardware solution to Spectre, which “tricks other applications into accessing arbitrary locations in their memory.” Processor firmware updates can mitigate the issue to some degree. Software also needs to be hardened to guard against it.
What’s a kernel?
The kernel inside your operating system is basically an invisible process that facilitates the way apps and functions work on your computer, talking directly to the hardware. It has complete access to your operating system, with the highest possible level of permissions. Standard software has much more limited access. Here’s how The Register puts it: “Think of the kernel as God sitting on a cloud, looking down on Earth. It’s there, and no normal being can see it, yet they can pray to it.”
How do I know if my PC is at risk?
Short answer: It is. Yes, even if it’s a Mac.
Google says “effectively every” Intel processor released since 1995 is vulnerable to Meltdown, regardless of the OS you’re running or whether you have a desktop or laptop. (You can find a full list of affected Intel processors in this article.)
AMD processors aren’t affected by the Meltdown bug. Chips from Intel, AMD, and ARM are susceptible to Spectre attacks. AMD says its hardware has “near zero” risk to one Spectre variant because of the way its chip architecture is designed, but AMD CPUs can still fall prey to another Spectre flaw.
Unsure if you’re already protected against Meltdown and Spectre? Gibson Research’s easy-peasy, free InSpectre tool lets you know if you’ve already installed the necessary operating system and processor updates on your computer.
Is there malware that exploits Spectre and Meltdown?
Yes, though it doesn’t appear to be serious at the moment. AV-Test, an independent antivirus testing house, is reporting that they’ve seen about 139 separate code samples that exploit the vulnerabilities. They include the first JavaScript-based proof-of-concept exploits attacking browsers. Basically, analysts believe that malware writers are investigating whether they can use these vulnerabilities to attack PCs, but they’re at the prototype stage.
How do I stay safe?
 Thinkstock
ThinkstockUpdate all the things. The entire computer industry is moving as quickly as possible to patch in Meltdown and Spectre protections. Right now, you should update your operating system and web browser pronto, and maybe your CPU’s firmware. We’ve created a separate guide to staying safe from Meltdown and Spectre attacks if you need more in-depth help.
The best overall antivirus suite
Norton Security Premium

 Read our reviewPrice When Reviewed:$109.99Best Prices Today:$55 at Symantec
Read our reviewPrice When Reviewed:$109.99Best Prices Today:$55 at Symantec
Definitely make sure you’re running security software as well—advice that Intel also stresses. No known Meltdown and Spectre attacks have been seen in the wild, but that’s sure to change now that the details are public. Triggering the attacks requires hackers to have access to your PC. An antivirus suite keeps bad guys off your PC. And as always, only download software and apps from reputable sources to reduce the risk of malware infection.
[ Further reading: The best antivirus for Windows PCs ]
What patches are already available?
Here’s where things get complicated.
Microsoft pushed out a Windows update protecting against Meltdown on January 3, the day that the CPU exploits hit headlines. Updates issued outside of Microsoft’s monthly “Patch Tuesdays” are rare, underlining the severity of this issue.
Intel also published fast firmware updates for its processors, but the first round of Spectre CPU fixes could cause system instability, reboots, and potential data loss or corruption in Intel CPUs released since 2011. Intel yanked them, Microsoft has released an optional emergency Windows patch that disables Intel’s earlier firmware updates if you installed them and are running into performance issues. Intel has since released revised patches for Intel Skylake (6th-gen) and newer systems. PC owners with other Intel CPUs should still hold off installing CPU firmware updates for now.
When processor firmware updates become available, you’ll need to snag them from your PC, laptop, or motherboard maker (like HP or Gigabyte) rather than Intel itself. Here’s how to find Spectre CPU fixes on DIY PCs.
 Adam Patrick Murray
Adam Patrick MurrayMacs are affected by Meltdown and Spectre, too.
AMD plans to release firmware updates to protect against Spectre, with patches for Ryzen, Threadripper, and Epyc CPUs coming first, and older architectures later. They’re classified as optional, though, because AMD says its CPU architecture has “near-zero” risk against the Spectre variant that requires a firmware update.
Apple quietly protected against Meltdown in macOS High Sierra 10.13.2, which released on December 6, as well as in iOS and tvOS 11.2. Kernel patches are also available for Linux.
The best overall online backup service
iDrive Online Cloud Backup

 Read our reviewPrice When Reviewed:$79.50Best Prices Today:$79.50 at iDrive
Read our reviewPrice When Reviewed:$79.50Best Prices Today:$79.50 at iDrive
Chromebooks received protection in Chrome OS 63, which released on December 15. You can find a detailed list of how individual Chromebooks are affected here. Furthermore, the Chrome web browser itself was updated to include an opt-in experimental feature called “site isolation” that can help guard against Spectre attacks. Site isolation is trickier on mobile devices; Google warns that it can create “functionality and performance issues” in Android. Chrome 64 included more mitigations.
[ Further reading: The best web browsers ]
Other browsers are battening down the hatches against Spectre as well. Firefox 57 released in November with some initial safeguards, and Edge and Internet Explorer received an update alongside Windows 10. On January 8, Apple pushed out updates to iOS 11 and macOS with “security improvements to Safari and WebKit to mitigate the effects of Spectre.”
Nvidia swiftly released graphics card drivers containing initial protection against Spectre as well—a crucial fix since GPU display drivers sink deep hooks into your kernel. Grab the latest Nvidia drivers here.
Check out PCWorld’s guide to protecting your PC against Meltdown and Spectre if you need more help. Gibson Research’s dead-simple (and free) InSpectre tool can let you know instantaneously if your PC has the necessary operating system and CPU patches installed.
Will these fixes slow down my PC or Mac?
It’s complicated, and highly dependent on your hardware, operating system, and workloads.
More recent Intel processors from the Skylake (6th-gen Core 6xxx series) era onward have a technology called PCID (Process-Context Identifiers) enabled and suffer less of a performance impact, according to Microsoft. Your version of Windows makes a difference as well. Plus, some applications—most notably virtualization and data center/cloud workloads—are affected more than others. Intel confirmed that the performance loss will be dependent on workload, and “should not be significant” for average home computer users.
Microsoft offers a slightly different and more nuanced opinion.
 Gordon Mah Ung
Gordon Mah UngIntel processors have a severe kernel security flaw.
Windows chief Terry Myerson says they “don’t expect most users to notice a change” on Windows 10 systems running Intel 6th, 7th, or 8th-generation Intel processors.
Intel published some post-patch benchmark results on best-case PCs like this on its blog. The tests showed an average performance loss of between 2 and 7 percent in the SYSMark 2014 SE benchmark, which simulates productivity tasks and media creation. Its responsiveness score—which measures “‘pain points’ in the user experience when performing common activities”—plummeted by a whopping 14 percent, though. In web applications that use heavy amounts of JavaScript, Intel saw a 7 to 10 percent performance loss post-patch. These tests were performed on SSD-equipped systems; Intel reports the performance loss is less noticeable if you’re using a traditional hard drive.
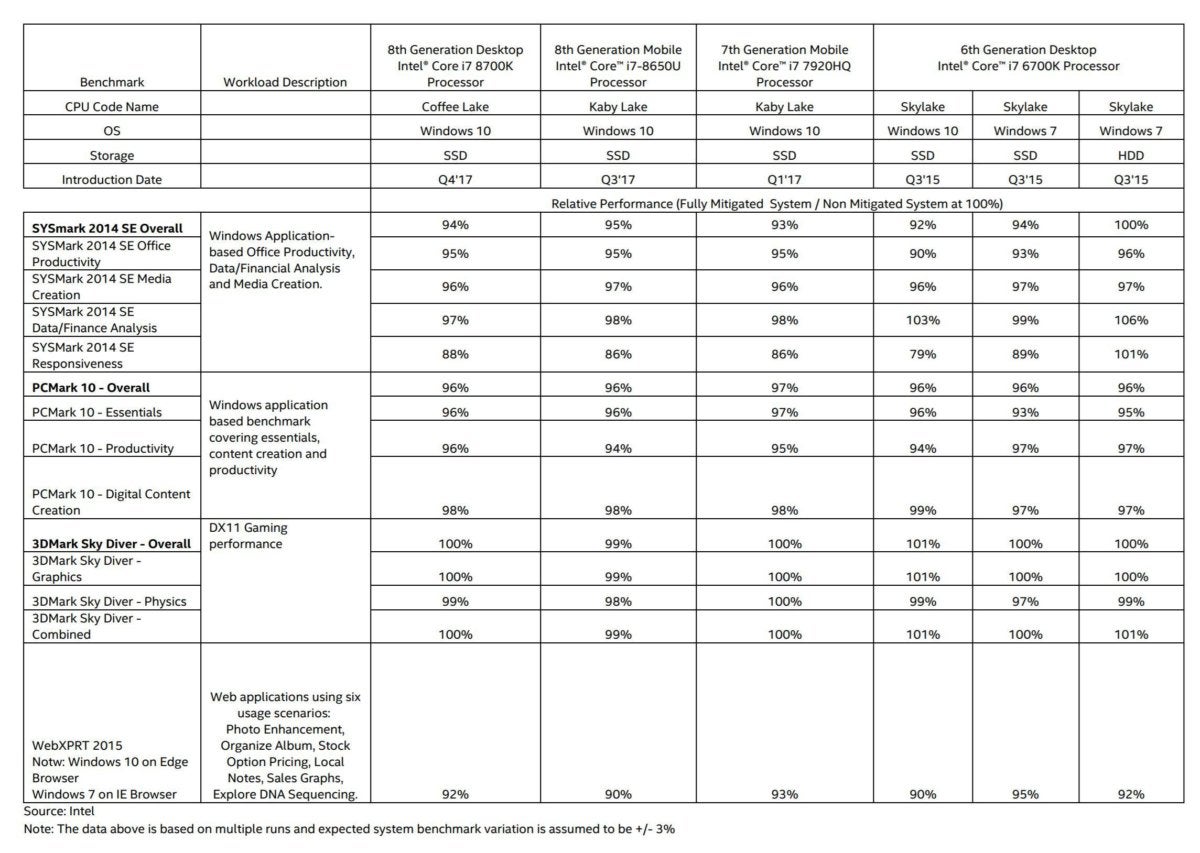 Intel
Intel Intel’s post-patch performance results on “best-case” PCs. Click to enlarge.
Those are the best-case scenarios, though.
If you’re running older processors, including 5th-gen Haswell chips, “some benchmarks show more significant slowdowns, and we expect that some users will notice a decrease in system performance,” Microsoft reports. Finally, Microsoft says for PCs running one of those older Intel CPUs and the older Windows 7 or 8 operating systems, “we expect most users to notice a decrease in system performance.” As far a business use cases, Windows Server “shows a more significant performance impact when you enable the mitigations to isolate untrusted code within a Windows Server instance.”
“Obviously it depends on just exactly what you do,” Linux creator Linus Torvalds wrote in the Linux Kernel Mailing List. “Some loads will hardly be affected at all, if they just spend all their time in user space. And if you do a lot of small system calls, you might see double-digit slowdown.”
PCWorld has tested Intel’s processor firmware patches on both a modern Surface Book and an older Broadwell CPU-based laptop. The performance impact of the patches range from negligible to downright ugly depending on the task being performed and your PC configuration. Want more concrete results for your specific system? Here’s how to test Meltdown and Spectre’s performance impact on your PC.
Will my games get slower?
Nope, according to the limited testing performed so far, though these sources didn’t test the Meltdown and Spectre patches with updated CPU firmware.
Phoronix tested Dota 2, Counter-Strike: Global Offensive, Deus Ex: Mankind Divided, Dawn of War III, F1 2017, and The Talos Principle on a Linux 4.15-rc6 machine with a Core i7-8700K and Radeon Vega 64. None saw a frame rate change outside the margin of error range.
[ Further reading: The best graphics cards for PC gaming ]
Hardware Unboxed tested a handful of DirectX-based Windows games in the video linked above. With DirectX hooking so deeply into Windows, gamers were worried about a potential performance degradation there. Fortunately, Hardware Unboxed observed virtually no frame rate loss in Ashes of the Singularity, Assassin’s Creed: Origins, or Battlefield 1. Phew.
The Intel results cited in the previous section include both OS and firmware patches. It showed virtually no performance loss in 3DMark Sky Diver, a popular graphics benchmarking tool.
Are AMD processors affected?
 Gordon Mah Ung/IDG
Gordon Mah Ung/IDGMuch, much less than Intel chips. All modern CPUs are vulnerable to Spectre attacks, but AMD says that its CPUs have “near zero” risk to the variant causing performance slowdowns in Windows PC due to the way they’re constructed. Nevertheless, AMD is releasing CPU firmware updates to protect against it, though they’re classified as optional. Operating system and software updates will protect against the other Spectre variant.
Mentioned in this article
AMD Ryzen 7 1700 Processor with Wraith Spire LED Cooler
 Price When Reviewed:$329.00Best Prices Today:$195 at Amazon
Price When Reviewed:$329.00Best Prices Today:$195 at Amazon
There is “zero AMD vulnerability” to Meltdown thanks to chip design, AMD says. If operating system patches exclude AMD CPUs from the new Meltdown-related performance restrictions—and Linux definitely is—the performance war between Intel’s chips and AMD’s new Ryzen CPUs may get even tighter.
Additional reporting by Mark Hachman


